In its yearly review of the identity landscape, the Identity Theft Resource Center (ITRC) suggests that, as others have hinted at, the walls really are crumbling when it comes to your identity’s safety.
As this reporter experienced, last summer, the possibility that your Personal Identity Information (PII) will wind up on the dark web is a Vegas-worthy, bet-the-house possibility.
Last year witnessed a record-breaking spike in data breaches, marking a worrying trend for cybersecurity. The ITRC’s tracking saw a 78% increase in 2023 compared to 2022.
However, a disturbing trend emerged: more than 1,400 public breach notices lacked crucial information about how the attack happened, representing a significant drop from the 100% transparency rate seen just five years ago. How did that Comcast hack happen? Who knows? The one involving T-Mobile? Your guess is as good as ours.
Companies are embarrassed by these thefts
The report suggests that even though nearly 11% of publicly traded companies faced compromises in 2023 — a worrying statistic on its own – transparency remained elusive.
Companies withheld attack details in 47% of cases compared to 46% for other organizations. This lack of openness makes it difficult to assess threats and hold entities accountable.
It’s also a reputational concern. Case-in-point is Norton Healthcare, which waited nearly six months before admitting to its patients that it had been the victim of a cyberattack.
Even though the company said that information that may have been impacted included names, contact information, Social Security numbers, birth dates, health information, insurance information, medical identification numbers, driver's license numbers or other government IDs, financial account numbers, and digital signatures, it opted to couch its breach to its customers as “We regret any inconvenience this incident may cause you.”
One reason why 2024 will be worse
The snowball effect of this is that more and more of us will see our PII on sale to anyone who wants to buy it.
It’s a safe bet, too, that Generative AI will also contribute to a rise in the sophistication of phishing attacks and other forms of identity fraud and scams using personal information stolen in data breaches, Eva Velasquez, executive director of ITRC, said.
While other "techsperts" think that AI will enable cybercrooks to leverage a person’s data in ways like voice cloning or deep fake videos, Velasquez thinks the opposite. That the sheer volume of personal data available via the dark web, coupled with the ability of hackers to employ AI to send out phishing emails and texts, is a much larger issue.
And, if 2024 repeats what the ITRC saw in 2023, consumers need to pay extra attention to four categories: healthcare, financial services, transportation, and utility companies – which, despite having fewer breaches – topped the list for estimated victims in 2023.
“Therefore, the probability of being hacked is unpredictable but on the rise unless you take measures to protect yourself,” suggests Miklos Zoltan, founder & CEO Privacy Affairs, a company that monitors personal data available on the dark web.
“By adopting a few straightforward rules and habits, you can make it more difficult for hackers to access your data and remove yourself from their line of sight.”
Telling the real from the fake
While AI can create convincing messages, there’s one way you can figure out which are real and which are not – one that seldom gets mentioned: take a quick look at the “who” and “what.”
Let’s look at the email below that a member of the ConsumerAffairs team received.
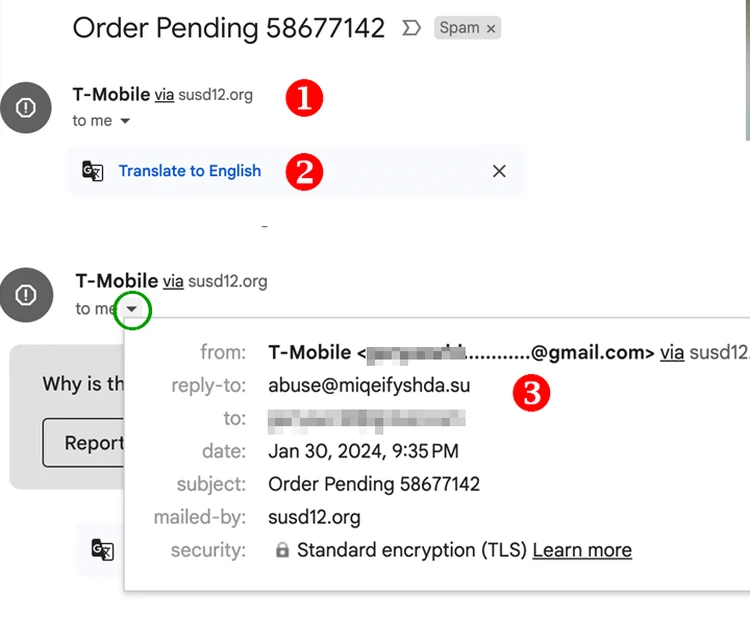
The email says:
It’s from “T-Mobile,” yet the “via” says it’s from “susd12.org” which happens to be the Sunnyside School District in Arizona. Not exactly “T-Mobile,” is it?
There's an attachment – a document that says “Translate to English.” Ask yourself why.
When you click on the triangle next to your name (“me”), it brings up the full details of the sender. The “reply to” doesn’t go to “T-Mobile” or the Sunnyside Schools, but rather to a website in Russia. A real T-Mobile email would come from a .com in the U.S.
As John Fahd, founder and CEO of ITegrators, explained, “If a scam email needs a reply from you, you'll see that the ‘Reply To’ field has a different email address than the one that actually sent you the email.”
“Scammers use this technique to get replies by enticing you to read and respond to the emails they send using the names of reputed brands, companies, governmental organizations, and so on.”
And you can’t beat common sense either. Ask “why” T-Mobile is sending you an invoice when you’re actually an AT&T customer. If a truly legit company really needs to get in touch with you and you don’t respond, trust us, they’ll find a way, probably by sending you a letter with a real request and a real phone number to contact.
Photo Credit: Consumer Affairs News Department Images
Posted: 2024-01-31 16:55:19